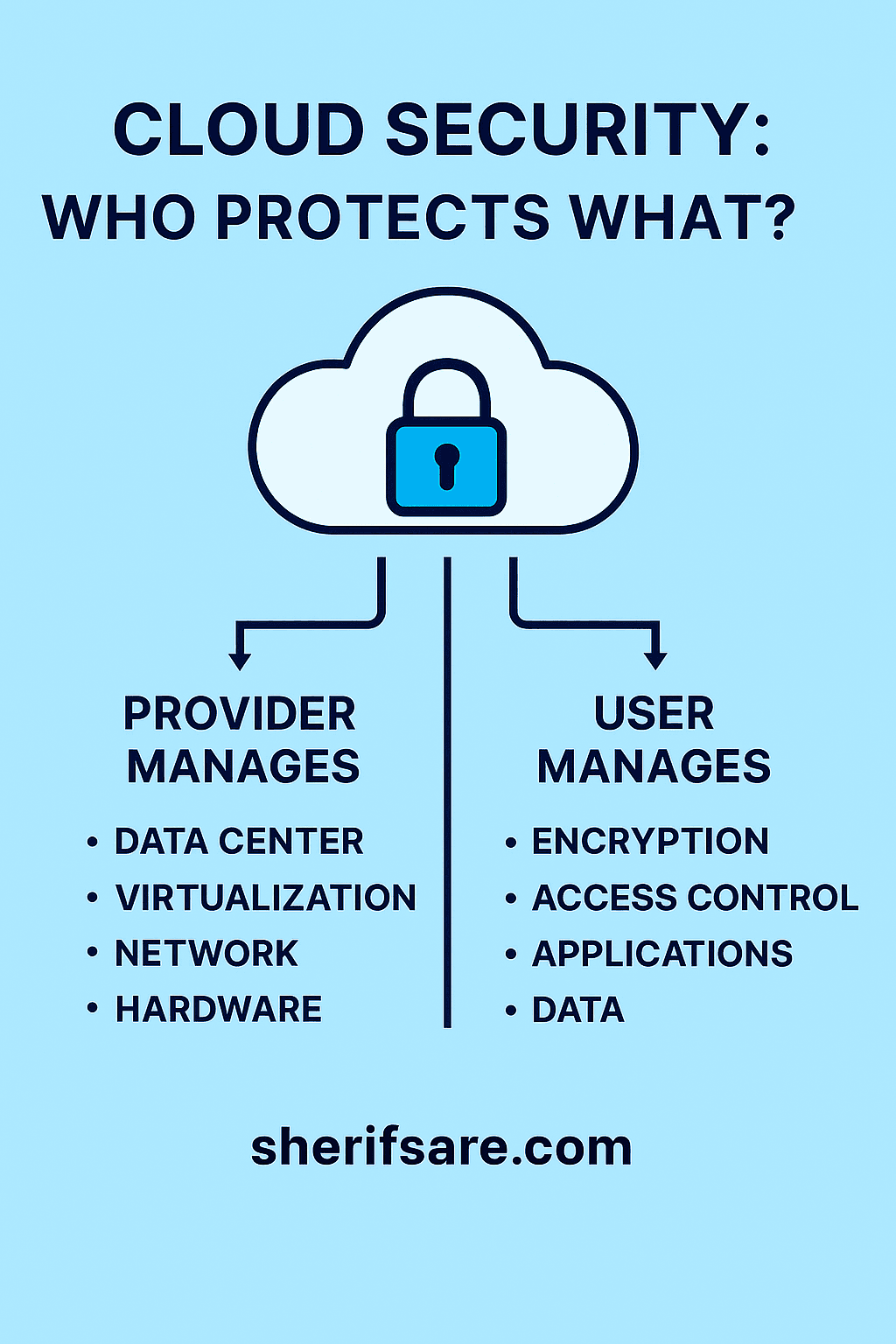
As businesses move to the cloud, cloud security becomes a shared responsibility. Providers offer robust infrastructure, but users must also play their part. Let’s break down how cloud security works and how to protect your data.
🛡️ Shared Responsibility Model
🔹 What Providers Handle
- Physical security of data centers
- Network infrastructure and firewalls
- Hypervisor and virtualization layers
- Compliance certifications (ISO, SOC, GDPR, etc.)
🔹 What Users Handle
- Access control and identity management
- Data encryption (at rest and in transit)
- Application security
- Monitoring and logging
Key Concepts
- Zero Trust Architecture: Never trust, always verify—every access request is authenticated.
- IAM (Identity & Access Management): Define who can do what, and enforce least privilege.
- Encryption: Use strong encryption for sensitive data, both in storage and during transmission.
- Multi-Factor Authentication (MFA): Add layers of protection beyond passwords.
Final Thought
Security isn’t just a feature, it’s a mindset. In our next post, we’ll explore cost optimization in the cloud and how to avoid overspending while scaling smart.